The OSINT Exposure of Offshore Oil Platforms
Offshore oil platforms, also known as oil rigs, are large industrial control systems meant to pull and process oil and natural gas from the sea bed beneath. Because these platforms are, as the name states, offshore, they usually provide long-term accommodations for an entire workforce.

It is hard to picture just how large these platforms truly are until you see something of normal size beside them like these supply vessels.

Because Oil platforms are basically offshore industrial control systems arguably farming our most important natural resource, there is a high risk of physical attacks like destruction, kidnapping and piracy, as well as cyberattacks. As digitization, remote monitoring, autonomous systems, and IoT connectivity increases on the platforms, so do the odds of a cyberattack.
As a caveat, I am writing this blog not from a stance of “let’s go hack platforms!” but rather, to illustrate why we need to be highly aware of what is possible from an OSINT perspective because it can be the first step in many forms of attacks.
Information Disclosures
The small bits of data leaked on social media, company websites, and by third-party organizations are of tremendous value to an attacker. With the high stakes involved, oil rigs have strict security rules regarding phones and filming/photography on board. It only took me a few minutes to find a walkthrough tour of an oil rig where the guy filming actually says “I am going to film this and put it on Facebook, even though we aren’t supposed to take videos.”

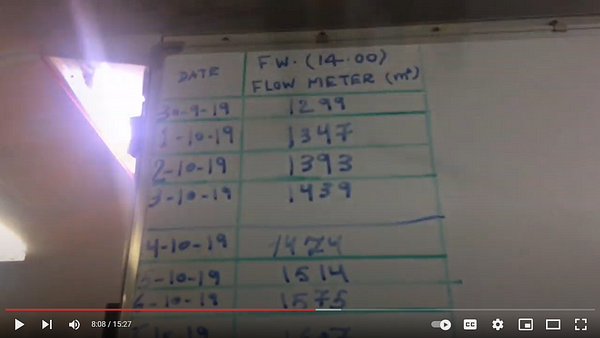
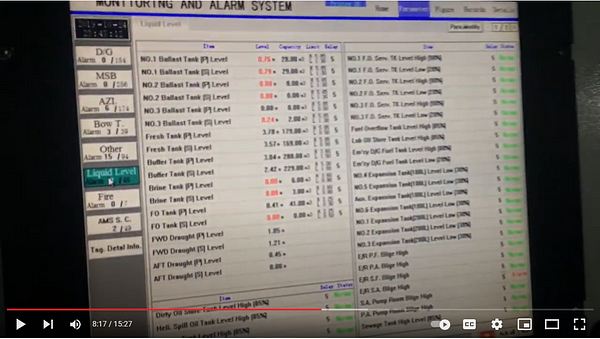
Another video from a platform in Saudi Arabia gives details about the flow meter, shows technology used on the rig, and zooms in on computer screens for the Monitoring and Alarm System. At one point, a man even walks in front of the camera showing the full name of the company he works for. Just knowing his name from the YouTube video, the company he works for, and that he has access to all parts of the rig, we could figure out which rig he is on and potentially gain access to the systems or the physical rig itself.


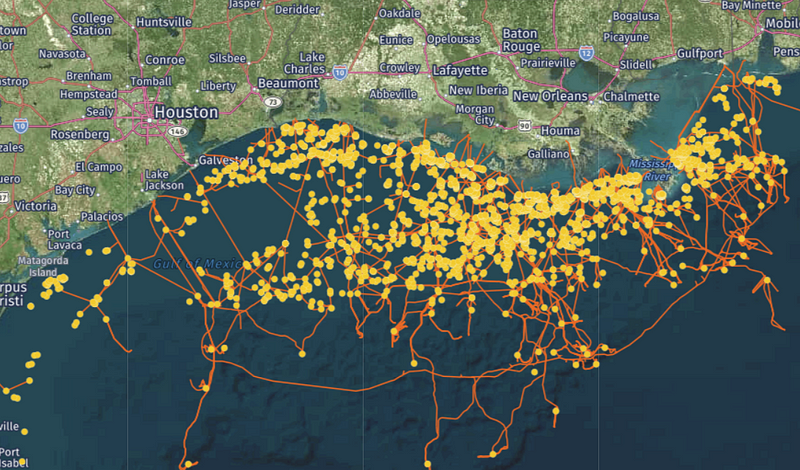
Many times combining data we find can illuminate a larger picture of the innerworkings or pattern of life around a rig. Heavy-lift vessels are used to move a platform from one area to another either by “dry-tow” out of the water or “wet-tow” within the water. Additionally, Platform Supply Vessels (PSVs) or Offshore Supply Vessels bring food and other necessities for the workers living on the platform. We can find lists of these vessels on third-party websites, and all of these vessels can be tracked if they are transmitting AIS signals during their operations.
Below is the Russian flagged “Ivan Sidorenko” IMO: 9624213 sanctioned in 2021 in connection to Russian Energy Export Pipelines. Just like tracking a human subject, watching the routines of a vessel over time can tip us off to places in the ocean they make frequent stops, such as a platform.
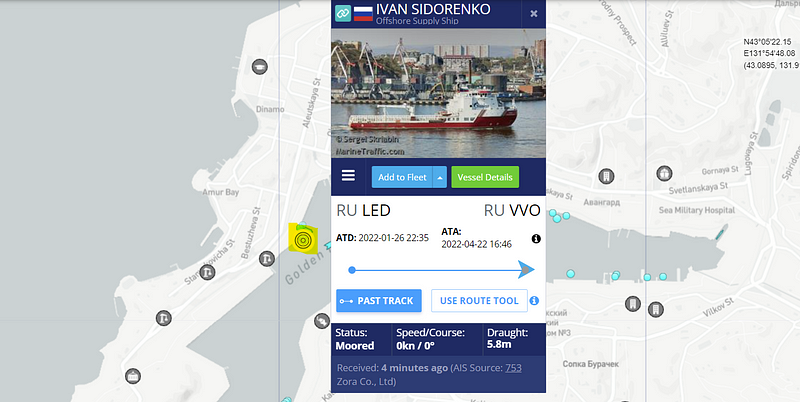
Tracking vessels is a great way to figure out what third party companies are servicing a platform as well as pinpointing exactly where a platform is located. However, there are easier ways to find the platforms, one way is finding their callsign and tracking their signal in something like marinetraffic.com, the other is by using interactive maps.
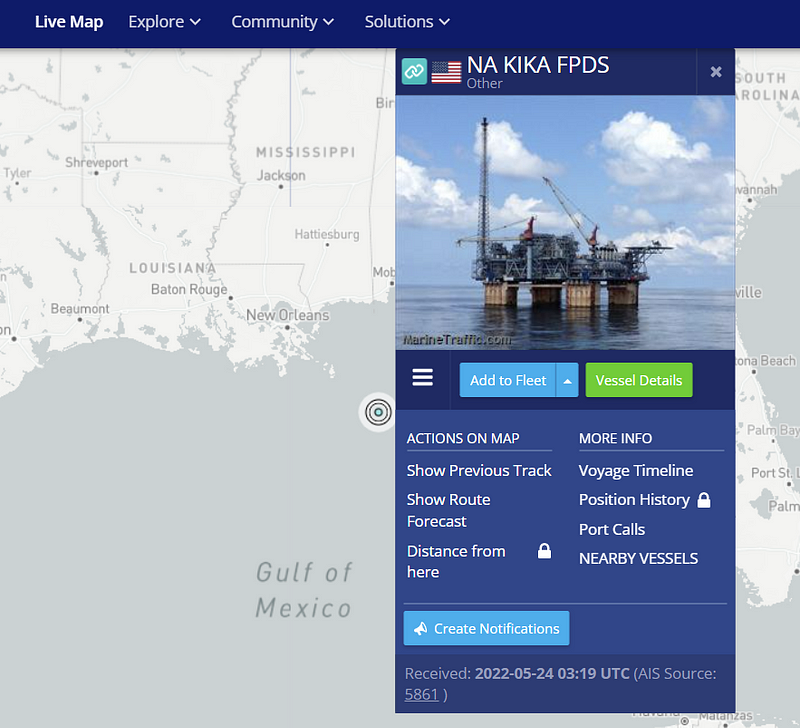
Interactive Maps
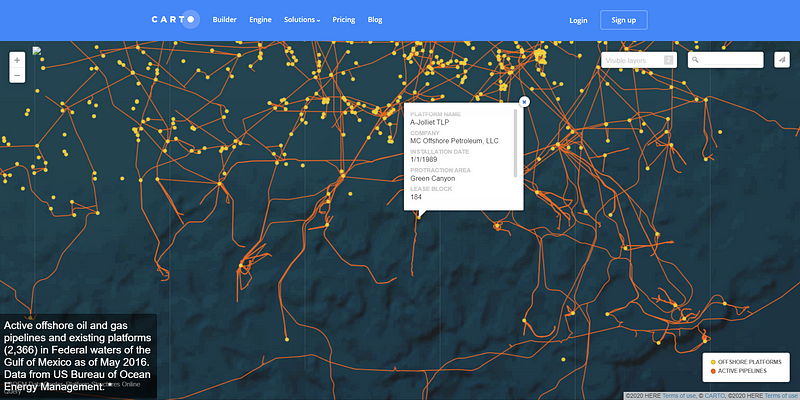
Skytruth Gulf of Mexico Offshore Platform and Pipeline Map offers an interactive map of the platforms and pipelines in the Gulf of Mexico. Clicking on each site or line shows a pop-up of ownership, area, length, etc.
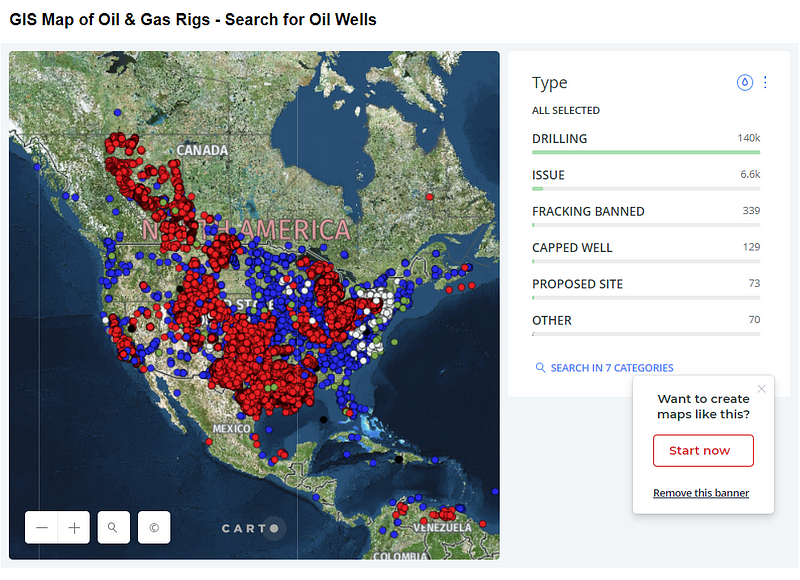
Drillingmaps.com features several maps including Oil & Gas, Refineries, Fracking, Power Plants, and Solar Energy Maps that are clickable to show the name, ownership, location, and more.
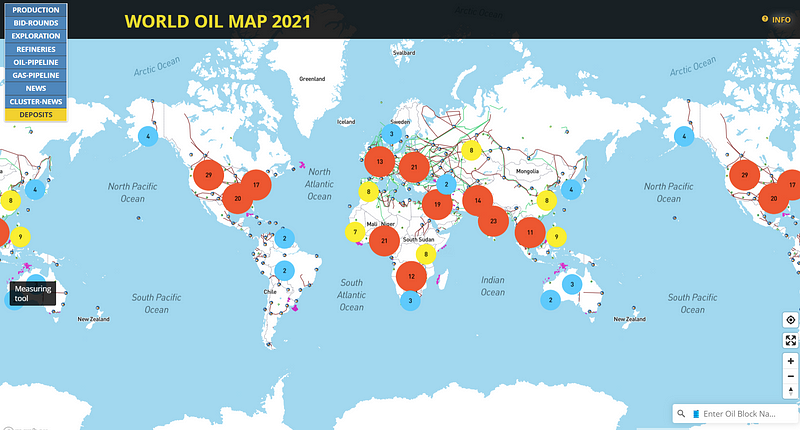
World Oil Map does not feature platforms, however, I included it because it is an International map that has many cool features like production fields, pipelines, refineries, exploration areas, and related news like in the image below.
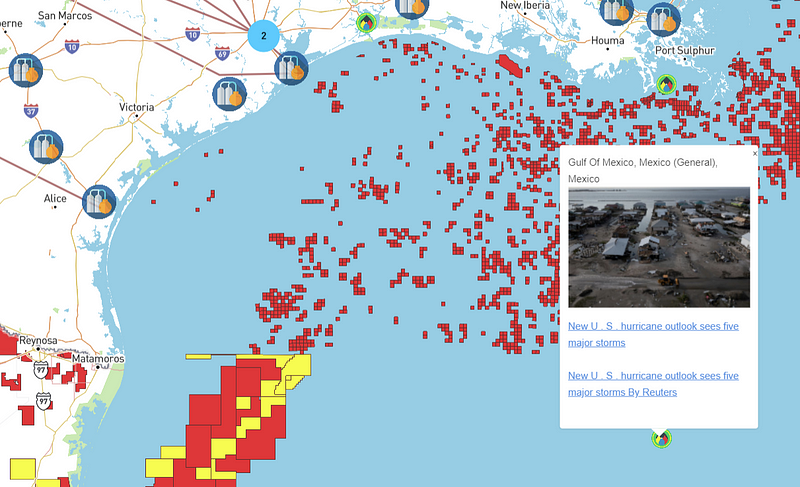
There are many other interactive maps available but these show some of the key information that attackers can derive through OSINT combined with other data from information disclosures and social media.
Social Media
Never underestimate the value of social media and what can be found there. Workers are often stuck on these offshore platforms for long periods of time and find ways to entertain themselves with videos, tiktok, Instagram, and forum posts all containing inside details of the offshore rigs. Simply doing a search on all the platforms for the name of the rig is bound to turn up something useful.

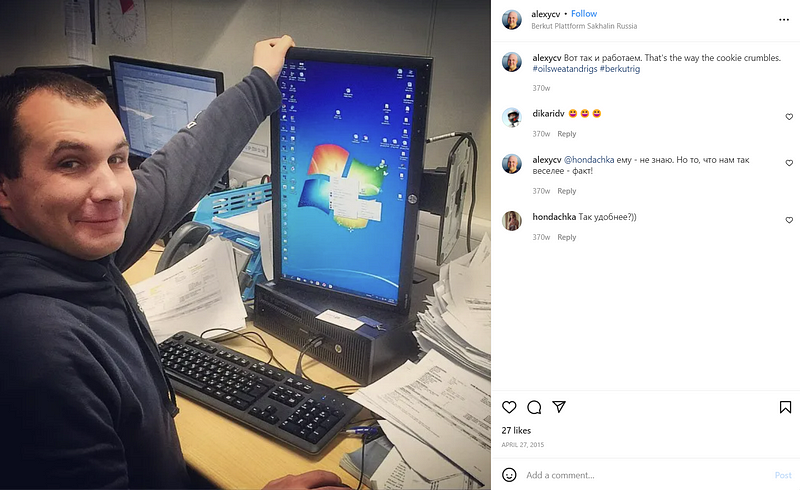
As a final thought, many of the systems featured in the above information leaks use default credentials, the systems are not updated and patched regularly, and they face the internet unneccesarily. Internet facing systems can be searched on Shodan and Censys for vulnerabilities that can then be leveraged and exploited by an attacker. Showing the brand name of a system in a video is just the map to the front door, the key is exploiting the often preventable vulnerabilities that exist within.
If you liked this blog, please sign up at raebaker.net to be notified when my new OSINT book, published by Wiley Tech, comes out in 2023. It is tentatively titled ‘Deep Dive’ and will cover OSINT fundamentals as well as dive deeper into topics such as Subject Intelligence, IoT, Industrial Intelligence, and Transportation Intelligence.