Investigating an Online Scam with SpiderFoot HX

In a recent blog article that I co-wrote with Tokyo_v2 titled Anatomy of a Puppy Scam, I track down a prolific puppy scammer selling fake tea-cup puppies online for thousands of dollars. The following is a breakdown of how I used Spiderfoot HX for much of my investigation into the domains and email addresses of the target website tiny-teacup dot com.
The Scan
This investigation into puppy scams began with just a single website, tiny-teacup dot com, so the first step was to analyze this site. I created a new scan within Spiderfoot HX and input the domain tiny-teacup dot com. I set the search to Scan Profile: All Modules vs the Passive only scan because I intended to collect as much information as possible and sift through it. I selected the box below to ensure Spiderfoot sends me an email notification upon completion. This decision turned out to be a wise choice because the scan was so unexpectedly large it took 5 hours. I was, however, perfectly happy to wait for Spiderfoot to crawl through all that data.
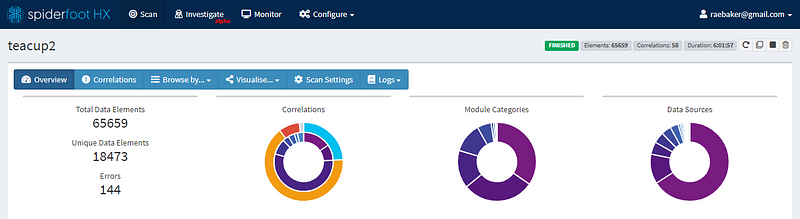
Ultimately, when the scan was complete, Spiderfoot HX found over 65,000 data points to investigate further. At first, this number was overwhelming but Spiderfoot helps by breaking the data down into easily digestible data sets and provides several different methods for visualizing data.
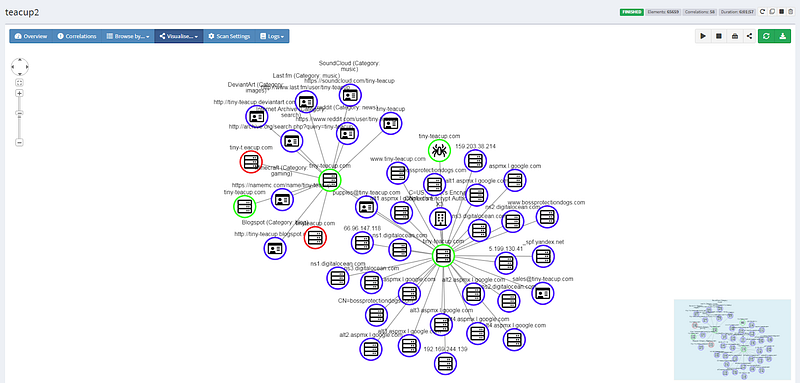
One of my favorite methods of viewing data is by Node Graph which shows the connections and data structure. Nonetheless, this search had so much data that I was unable to view the whole thing at once. Fortunately, I was able to view selections of the whole graph in more detail and this helped me to understand the relationships between entities.
Breaking it Down
Using the “Browse by” dropdown menu at the top of the screen, I select “data type” which provides me with all sorts of interesting things to look at like Domain Whois, Email Address, Co-Hosted Sites, Human Names, Malicious Affiliates, etc.
I decided to start looking through the co-hosted sites because my goal was to find connections between tiny-teacup dot com and other known scam sites. Co-hosted sites often indicate sites hosted within the same server, infrastructure, or behind the same firewall. These related sites can be used as new leads in the investigation, providing a broader investigative surface to look through. I was, however, cautious to jump to conclusions since co-hosted sites do tend to lead to false positives. If a site were to reside behind a service like Cloudflare, we would tend to see many other sites connected that may not have any real connections within the investigation.
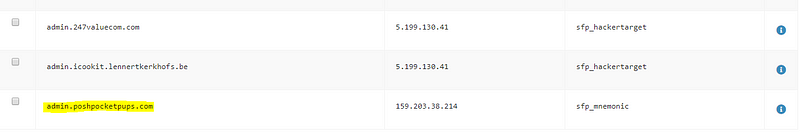
The co-hosted site search yields a lot of results but the one I am most interested in is “poshpocketpups dot com.” I have seen this domain mentioned alongside tiny-teacup in many online complaints stating that people had been scammed by the same person that was named in the Tiny-Teacup scams.
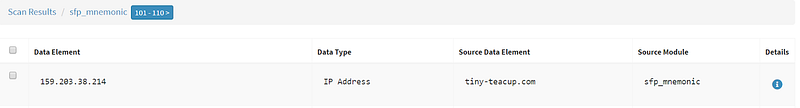
I found something interesting by selecting Browse By: Module in the top bar and scrolling down to select sfp_mnemonic, which is a Passive DNS service that has a database of historic resolutions of names to the same IP address as the one Tiny-Teacup uses. If I look at the first IP address in the list and click on the details button I am presented with a node graph of all the hosts and domains that resolved to Tiny-Teacup’s IP address.
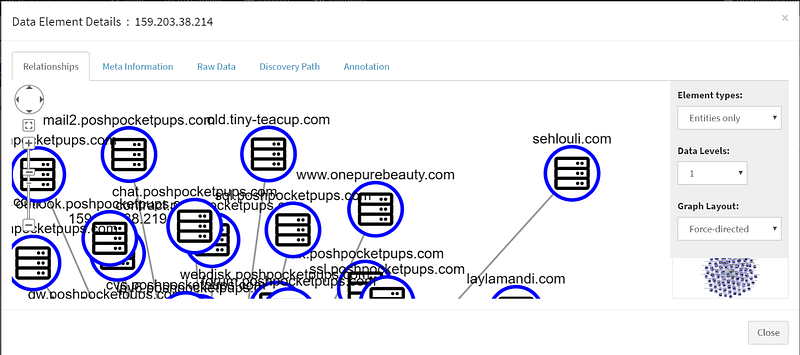
One of the addresses stood out to me — sehlouili dot com. According to the contents of the website, it’s for Mehdi Sehouli who is advertising his personal Freelancer, Full-Stack Web Developer, and Consultant business. In the About Me section of the site, it mentions creating bots for various systems and when I Google the name, this listing below pops up for a puppy on PoshPocketPups written by Mehdi Sehouli, our Freelancer.
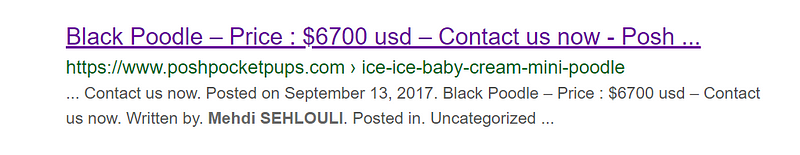
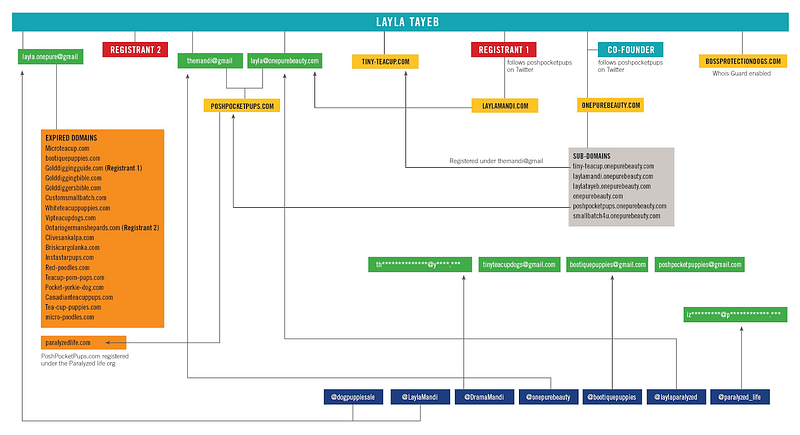
Again, one must use caution when looking at co-hosted and resolved sites because shared hosting platforms can cause innocent sites to show up on these searches, so you will want to be sure you have multiple correlations to support theories of attribution you are developing. However, Mehdi’s domain resolves to several of our targets like Bossprotectiondogs, Poshpocketpups, tiny-teacup, and Onepurebeauty who have all been shown to have connections to Layla Mandi and our scam based on a (detailed further in my investigation blog post). I designed a chart to help me keep track of the various domains, emails, and social media accounts I linked together.
Human or bot?
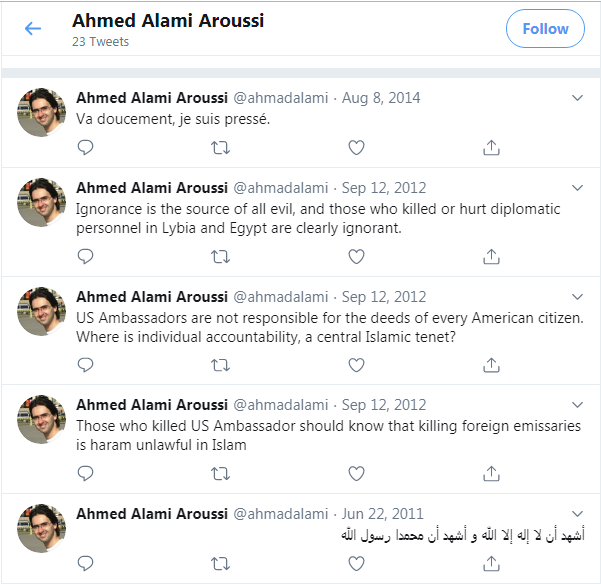
Next, I decided to look through the human names that Spiderfoot scraped from the Tiny-Teacup website to see if they are real people. The names found also happen to be the “reviewers” on the site and I need to verify whether the reviewers are legitimate people. Using the details button next to the name provides me with a node graph of accounts for the human Ahmad Alami.
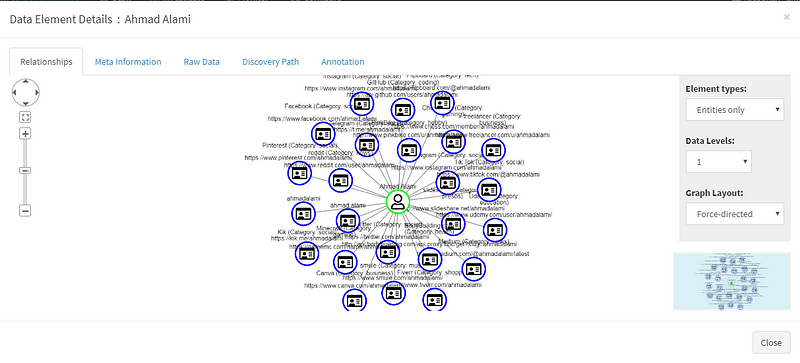
Being mindful of potential false positives, I start going through every one of these accounts and verifying them. Most of these accounts have no information or posts associated with them and these are the ones that do appear to be bot accounts. Based on these findings, I believe that all of the reviewers are a mix of either bots or false positives. I was able to use the data I found in Spiderfoot to search through social media sites including Facebook, Instagram, and Twitter to verify the legitimacy of the data I found. One example of what appears to be bot activity is below:
Using Analytics
Another way to use Spiderfoot data to track down domains owned by the same entity is through their Google Analytics codes. By selecting Web Analytics under Data Type I get a list of Google Analytics codes used on the domains picked up by the search on Tiny-Teacup.
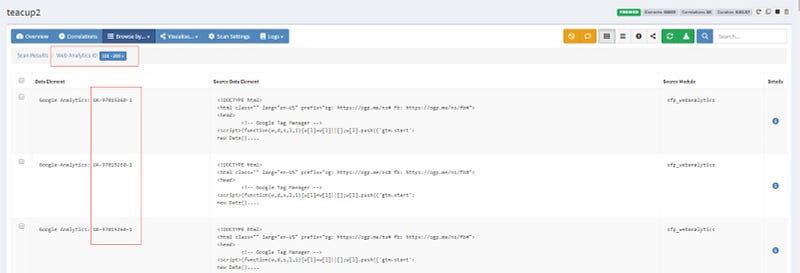
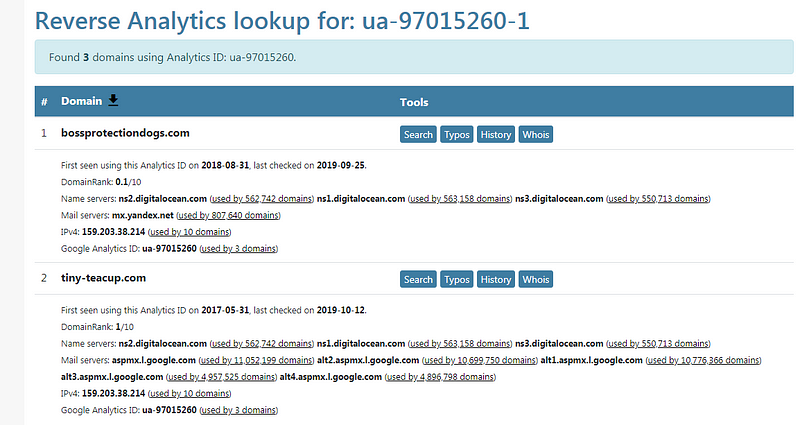
Spiderfoot integrates with SpyOnWeb using their API, however, in this case, SpyOnWeb did not have data pertaining to this analytics ID so I used an alternative source manually, DNSlytics. Because many domains utilize the same Analytics codes, this is a good way to show a connection between the management of multiple domains by the same entity. I was able to make definitive connections to sites previously known to be affiliated with my target domain but unable to find anything new.
Malicious IPs and Vulnerabilities
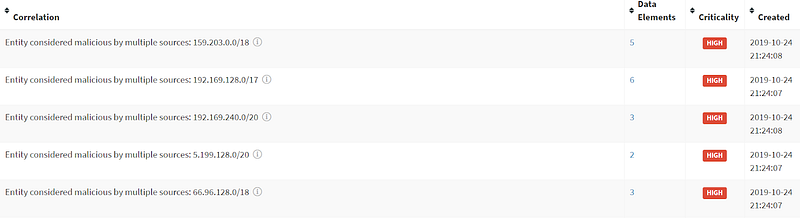
It is worth noting here that several sources list the neighboring IPs and network that Tiny-Teacup is on as malicious. These details can be found under Correlations as well as the modules Blacklisted Affiliate Sites and Malicious IPs on Same Subnet. These also fall under the same shared hosting warning as co-hosted sites, so use caution and verify your data is connected.
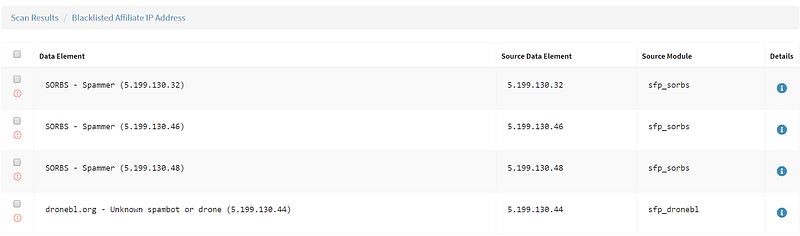
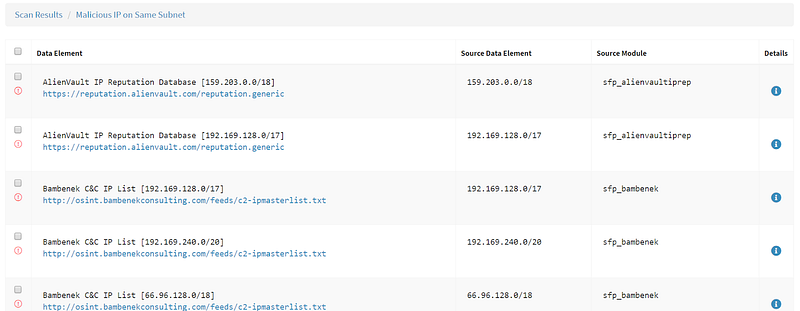
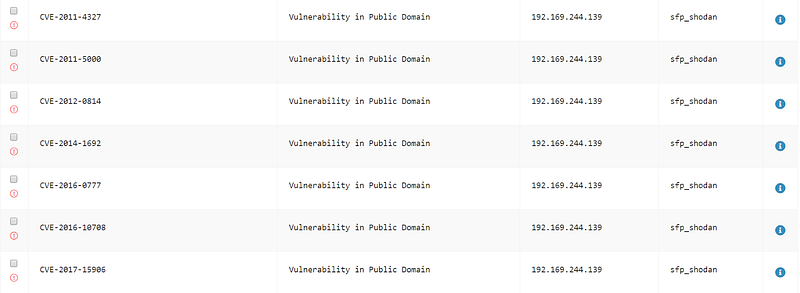
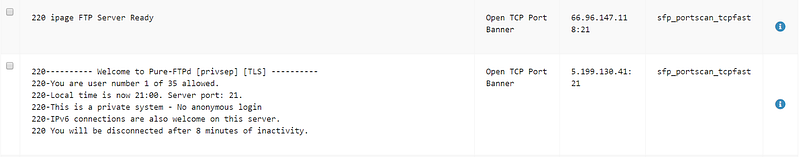
Additionally, using the Shodan API I am able to see several vulnerabilities listed for this IP address. This data would be useful for a situation where a more active search was being conducted and vulnerabilities like the internet-facing FTP and SQL servers could be (or already have been) exploited.

Conclusion
Starting from a simple domain search conducted in Spiderfoot HX I was able to use that data to link and verify 20+ scam domains to several registrants, along with their possible physical addresses and phone numbers. This allowed me to pinpoint vulnerabilities in their network that could enable exploitation and was also able to identify and validate fake reviewers via their social media profiles. When Spiderfoot was paired with some great APIs and some Google/People searching, an astounding amount of correlated information was brought to light. The information gathered in the Spiderfoot domain search was invaluable to the research into the Tiny-Teacup puppy scam as it showed the domain relationships, gave me multiple locations to dig into, and led me to a whole bunch of social media profiles that ultimately allowed for further expansion in my investigation from the sheer amount of useful data it provided.