Using Lampyre for Basic Email and Phone Number OSINT
***Due to recent findings by @MwOsint I can no longer endorse Lampyre as a trusted tool https://keyfindings.blog/2020/03/23/be-careful-what-you-osint-with/
Lampyre is a Windows-based Data Analysis tool that can be used for all kinds of analysis including Crime, Geographic, Cyber Threat, and Financial to name a few. I believe Lampyre is a great tool for OSINT beginners for three reasons:
- The data is easy to visualize in a schema
- No Linux is required
- It doesn’t require you to mess around with APIs
I am going to demonstrate a simple way to connect and visualize data from an email address and phone number. Lampyre does offer similar documentation on their website, however, I will provide some additional ways to use the information for OSINT purposes.
First, we will need to start a new investigation (or import one).
File>New Investigation. Save the file wherever you prefer.
This will open a blank investigation to begin your search.

To begin searching for a specific item, we need to open the list of requests. Windows>List of Requests
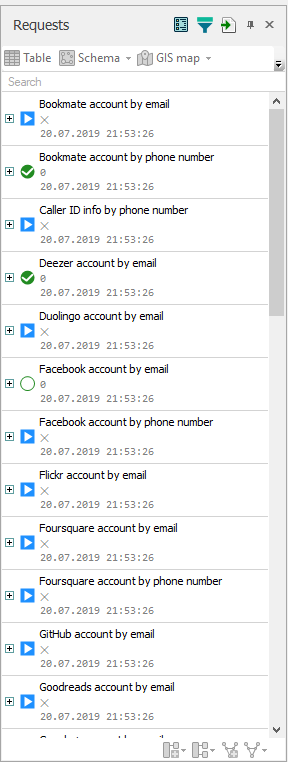
The List of Request window will pop up and allow you to select your search criteria. For this demo, we will select Email and Phone Number from the pane on the left. Once those are selected we will see specific parameters show up on the right that will allow us to input information. Enter your target’s email and phone numbers in those boxes. In the Tasks pane, you can specify which accounts/sites to search but as a general rule, I just check them all.
Once all those are added/selected hit Execute.

The requests will begin to turn green as they finish.
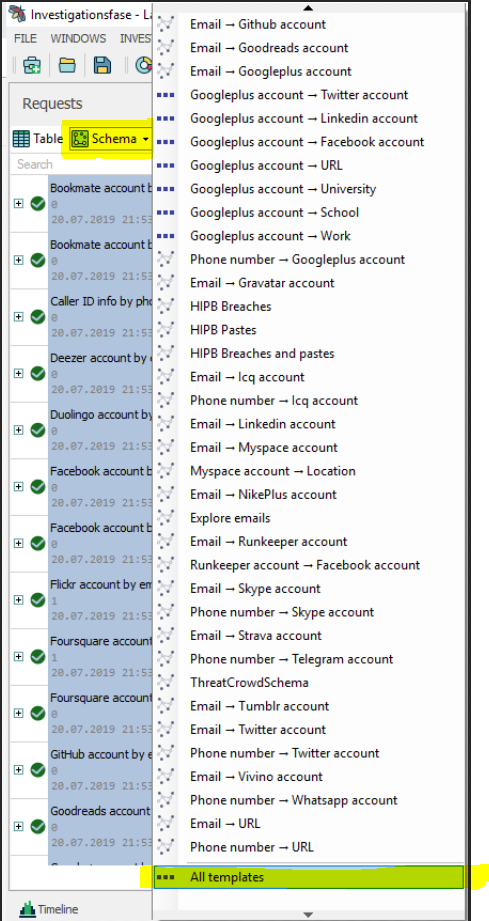
When all of the requests are finished, highlight the entire list, hit Schema at the top and scroll all the way down to the bottom where it says All Templates.
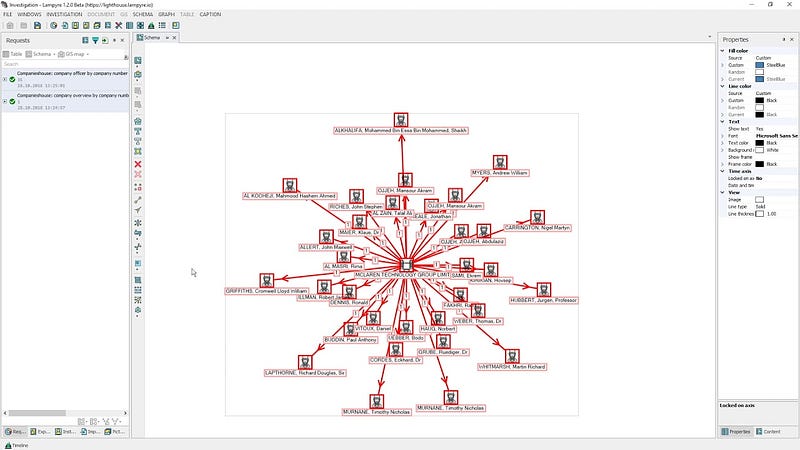
Selecting this will present you with a schema similar to the one below, this will obviously vary by the target. I have protected this person’s identity but you can see several interesting things that could be used in your OSINT research. A gravatar account could be useful in providing additional information as well as links to other accounts, Flickr might be used to gather intel on the target’s family or friends, a Foursquare account may allow you to geolocate a target or provide you with additional information, and Runkeeper could offer the target’s workout patterns or location.
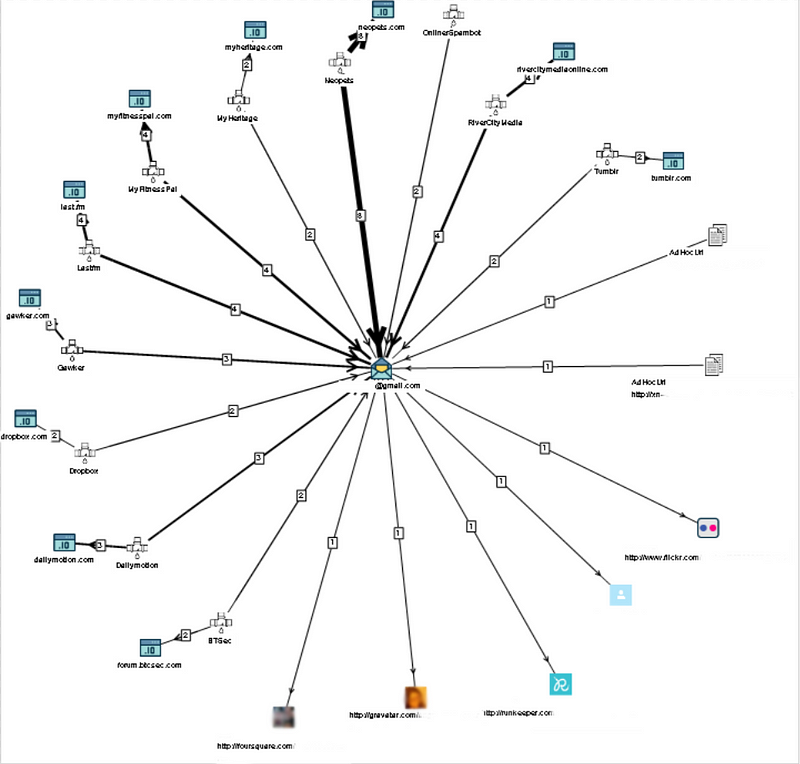

An additional source of data found in the schema that you could use is information collected in data breaches. Here is a great 10 Minute Tip video by Micah Hoffman (@WebBreacher) on how to use breach data that can be found on the OSINTCurio.us YouTube page.
Overall, Maltego seems to be the go-to program for a more in-depth analysis, but I found Lampyre to be super easy and accessible for basic email recon without having to fuss with APIs. I think that anyone starting out in OSINT will benefit from playing around with this tool to practice pivoting from information gathered. My only wish is that Lampyre would provide more video tutorials for analyzing the data.
The above info is for educational purposes only.